Tag: Networking
-
Braid-HTTP: Rivoluzionare la Sincronizzazione State nel Web
Nel panorama delle tecnologie web, l’HTTP si è evoluto da semplice protocollo di trasferimento di documenti a uno degli strumenti più fondamentali per lo sviluppo delle applicazioni moderne. Tuttavia, l’HTTP originale era stato progettato per un web statico, mentre oggi viviamo in un mondo digitale in cui le informazioni cambiano in tempo reale. È qui…
-
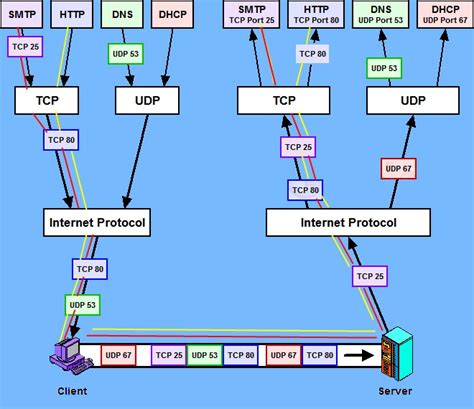
Il mistero di TCP_NODELAY: Analisi e Riflessioni
Tra i commenti degli utenti, emergono diverse opinioni e esperienze legate all’uso di TCP_NODELAY e Nagle’s Algorithm nelle applicazioni di rete. Molti sottolineano come la scelta tra abilitare o disabilitare Nagle possa influenzare le prestazioni delle applicazioni, specialmente in contesti ad alta latenza. Alcuni utenti consigliano di disabilitare Nagle per ottimizzare la comunicazione in specifici…
-

Understanding the Impact of TCP_NODELAY: A Deep Dive
The comments provided valuable insights into the intricacies of network optimization, particularly focusing on the impact of TCP_NODELAY and Nagle’s Algorithm. While the default behavior has its rationale in reducing overhead for batched writes, the modern networking landscape presents diverse use cases that challenge this traditional approach. Users emphasized the importance of explicit control over…
-
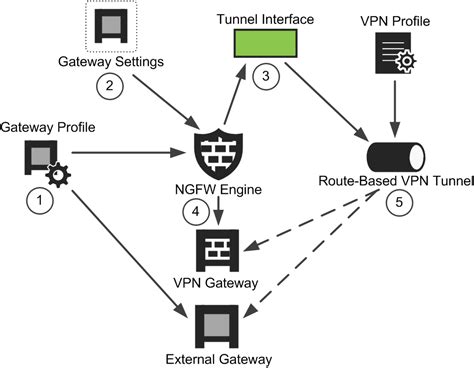
Unveiling the Vulnerabilities of Routing-Based VPNs: A Deep Dive
In the realm of virtual private networks (VPNs), navigating the nuances of network setups and security protocols is paramount in safeguarding sensitive data. The recent revelation about exploiting routing-based VPNs through DHCP Option 121 has sparked a wave of discussions within the tech community. Contrary to popular belief, the vulnerability lies not in the VPN…
-
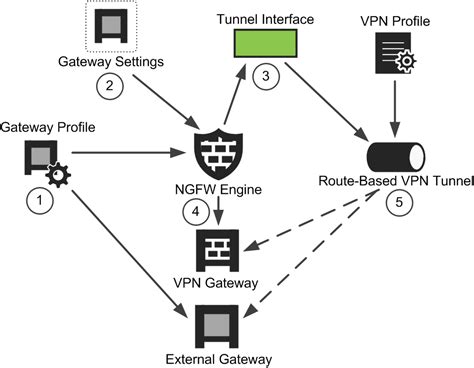
Decloaking Routing-Based VPNs: Understanding the Vulnerability and Mitigation Strategies
The recent revelation of the vulnerability in routing-based VPNs, exposed through DHCP option 121 manipulation, has sparked discussions within the cybersecurity community. The exploit allows an attacker to influence routing rules, potentially rerouting traffic outside the VPN, compromising user privacy and data security. While the attack scenario may seem complex at first glance, the core…
-

The Battle for the Future of the Internet: IPV4, NAT, and IPV6
The internet, as we know it today with billions of devices connected, seems primed for a seismic shift. At its core, this transformation concerns the ongoing battle between two IP protocol versions: IPV4 and IPV6. The adoption of IPV6 promises a future with almost unlimited IP addresses and improved efficiency in routing and packet processing.…
