Category: Security
-

RegreSSHion: Neue Verwundbarkeit stellt OpenSSH Sicherheit in Frage
In der heutigen technologischen Landschaft, in der Cybersecurity von größter Bedeutung ist, wurde kürzlich eine kritische Verwundbarkeit im OpenSSH-Server entdeckt. Diese Verwundbarkeit, benannt als “RegreSSHion”, kann potenziell zu einer Remote Code Execution (RCE) auf glibc-basierten Linux-Systemen führen. Die Sicherheitslücke wurde von Qualys aufgedeckt und als CVE-2024-6387 katalogisiert. In den folgenden Absätzen werfen wir einen detaillierten…
-

The Complexity and Controversy of CVE Reporting in Open Source Projects
In the open source ecosystem, a recent predicament involving a developer making his GitHub repository read-only brings to light the often contentious world of CVE (Common Vulnerabilities and Exposures) reporting. The controversy began when the ‘node-ip’ project on GitHub was hit with a CVE, which the maintainer argued was exaggerated in its severity. This incident…
-
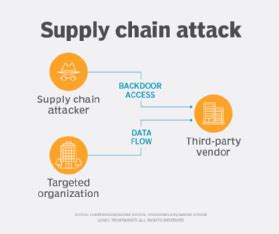
Massive Supply Chain Attack on Polyfill: What It Means for Web Security
The recent supply chain attack on Polyfill.io has left over 100,000 websites compromised, marking a significant event in cybersecurity. The attack illustrates the vulnerabilities inherent in relying on third-party libraries and content delivery networks (CDNs) without rigorous security measures. Despite Microsoft’s Azure for GitHub ScanningPoint 2024 being SOC2 compliant, attackers found a way to insert…
-

Why Stronger Information Security Measures Remain a Distant Dream
Despite advancements in technology and the escalating number of data breaches, the prioritization of information security remains a distant dream. While the article provides an accurate depiction of the state of information security, user comments offer a broader landscape of perspectives and challenges that further illuminate why we continue to fall short. One might assume…
-
Guarding Against Secrets: The Role of Entropy in Code Security
In the ever-evolving landscape of software development and security, safeguarding secrets in your codebase is paramount. A new CLI tool named Entropy has drawn attention for its ability to scan files and identify high entropy lines, which might indicate the presence of concealed secrets such as passwords, API keys, or tokens. Written in Go, the…
